Scareware is a term that is frequently used to refer to a cyberattack tactic that scares people into visiting bogus or infected websites or downloading malicious software (malware). Scareware may manifest itself in the form of pop-up advertisements that appear on a user’s computer or via spam email attacks.
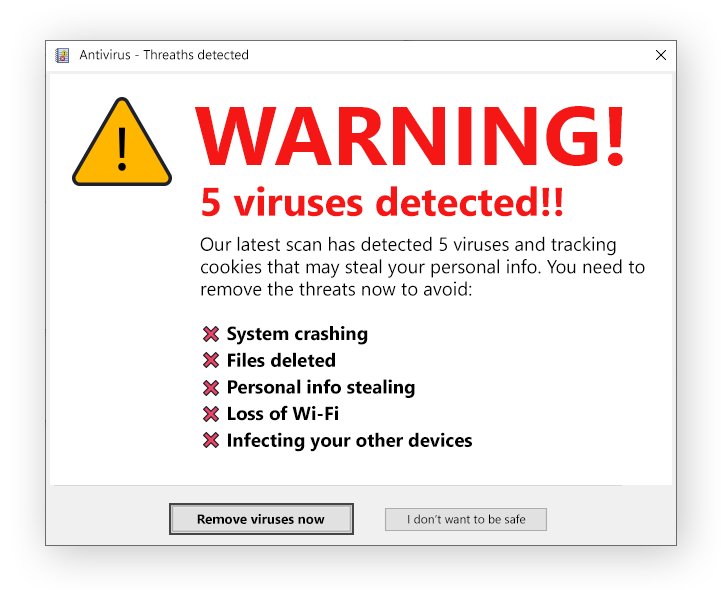
Scareware attacks are frequently launched via pop-up messages that appear on the user’s screen, informing them that their computer or files have been infected and then offering a solution. This social engineering technique is used to scare people into paying for software that ostensibly solves the “problem.” However, scareware, rather than resolving an issue, contains malware designed to steal the user’s personal data from their device.
Scareware can also be distributed via spam email, where users are duped into purchasing worthless goods or services. The information that hackers successfully steal is then used to expand their criminal enterprise, which is primarily focused on identity theft.
Ads and Pop-ups
So, what is scareware and how does it work? Typically, through rogue security providers’ pop-up ads that appear to be legitimate but aren’t. Advanced Cleaner, System Defender, and Ultimate Cleaner are examples of rogue scareware or fake software to avoid.
Scareware advertisements, which appear in front of open applications and browsers, are designed to make computer users believe they have a serious problem with their device. Pop-up warnings inform users that their computer has been infected with dangerous viruses that could cause it to malfunction or crash. Some scareware advertisements claim to scan the user’s device and then display hundreds of viruses that are allegedly present but are actually fake results. The scarier or more shocking an ad pop-up sounds, the more likely the claims it makes are scareware.
Scareware is also characterized by a sense of urgency. Hackers try to persuade users that a supposedly malfunctioning device necessitates immediate action, then urge them to install the program as soon as possible. As a result, be wary of any advertisement that requires the user to act immediately. It’s almost certainly scareware.
Scareware ad pop-ups, on the other hand, can be particularly difficult to remove from a user’s device. Hackers want the fake software to stay on a user’s screen as long as possible, so they make the close button difficult to find and display even more fake warnings when the user does.
How to Protect Yourself from Scareware?
The most effective way for users to avoid scareware is to only use software from legitimate, well-known, and well-respected providers. It’s also critical to avoid the so-called “click reflex.” In other words, ignore any unexpected pop-up ads, virus warnings, or invitations to download free software from an untrustworthy source.
If your device is infected with scareware, never click the “download” button and always close the ad carefully. Rather than attempting to click on the pop-up ad, it is preferable to simply close the web browser. On a Windows device, use Control-Alt-Delete to open the Force Quit window, and on a Mac, use Command-Option-Escape to open the Force Quit window. If that doesn’t work, force the device to shut down.
Another option is to use software such as pop-up blockers and URL filters to prevent users from receiving messages about fake or malicious software. Users will also be protected from scareware by using legitimate antivirus software, network firewalls, and web security tools. To provide effective protection against scareware and other types of malware, these tools must be kept up to date at all times.
Organizations can assist employees in avoiding scareware by providing regular training on how to recognize suspicious activity or software. Users must be on the lookout for telltale signs of a cyberattack, such as suspicious pop-up ads and email messages.
Scareware Removal
Scareware warnings and pop-up advertisements indicate that a user’s computer has been infected with malware. Scareware and other forms of malware must be removed with a third-party removal tool that can remove all signs of the virus infection, followed by re-enabling the antivirus software that the scareware bypassed or disabled in order to carry out its purpose.
The software provider’s latest patches and security measures must be installed on the computer and all software on the device.
Examples of Scareware
In 2010, the Minneapolis Star Tribune newspaper’s website began serving Best Western advertisements that directed users to bogus websites that infected their devices with malware. The attack displayed pop-up advertisements informing users that their device had been infected and that the only way to remove it was to download $49.95 software. Before being apprehended, the attackers amassed a total of $250,000.
Other types of scareware are device-specific. For instance, Mac Defender is an early form of malware directed at Mac devices, while Android Defender is scareware or phony antivirus software directed at Android phones.
How do I know if I have a fake virus?
Scareware is typically used to infect a computer with malicious software. Numerous unwanted pop-up ads or error messages, unexpected freezes, crashes, or restarts, icons appearing unexpectedly on the desktop, sudden device or file lockouts, a computer suddenly running slowly, and web browsers being set to a new homepage or with new toolbars are all telltale signs that a virus is present on a device.
Reputable software vendors and antivirus vendors do not employ scare tactics to compel users to download their products. As a general rule, avoid any software advertisement that sounds malicious or threatening and attempts to scare the user into downloading it.